type
Post
status
Published
date
Jul 20, 2023
slug
blog-84
summary
xv6 traps handling
tags
文字
整理
推荐
category
学习思考
icon
password
Property
Aug 13, 2023 04:24 AM
Traps and Sytem calls
There are three kinds of event which cause the CPU to set aside ordinary execution of instructions and force a transfer of control to special code that handles the event. We use
trap as a generic term for these situations- system call: when a suer program executes the
ecallinstruction to ask the kernel to do something for it
- exception: an instruction(user or kernel) does something illegal, such as divide by zero or use an invalid virtual address
- device interrupt: when a device signals that in needs attention, for example when disk shouldn’t need to be aware that anything write request
- Trap is transparent
Trap’s process
- A trap forces a transfer of control into the kernel
- The kernel saves registers and other state so that execution can be resumed
- The kernel execute approprate handler code
- The kernel restores the saved state and returns from the trap
- The original code resumes where it left off
- Xv6 handles all traps in the kernel, which means traps are not delivered to user code
- Handling traps in the kernel is natural for system calls.
- It makes sense for interrupts since isolation demands that only the kernel be allowed to use devices, and because the kernel is a convenient mechanism with which to share devices among multiple processes.
- It also makes sense for exceptions since xv6 responds to all exceptions from user space by killing the offending program
- Four stages Xv6 trap handling proceeds
- Hardware actions taken by the RISC-V CPU (
stvecwill be set in this step) - Some assembly instructions that prepare the way for kernel C code
- A C function that decides what to do with the trap(
usertrap()andkerneltrap()) - The system call or device-driver service routine
- Three distinct cases:
- traps from user space
- traps from kernel space
- timer interrupts
Kernel code (assembler or C) that processes a trap is often called a handler; the first handler instructions are usually written in assembler (rather than C) and are sometimes called a vector.
RISC-V trap machinery
- some inportant registers
- sscratch: The kernel places a value here that comes in handy at the very start of a trap handler. (trapframe is put here in kernal)
- scause: A number that describes the reason for the trap will be put here .
- stvec: Address of its trap handler; the RISC-V jumps to the address in stvec to handle a trap. stvec → pc
- sepc: PC will be saved here (since the pc is then overwritten with the value in stvec) when a trap occurs. The sret (return from trap) instruction copies sepc to the pc. The kernel can write sepc to control where sret goes. pc → sepc
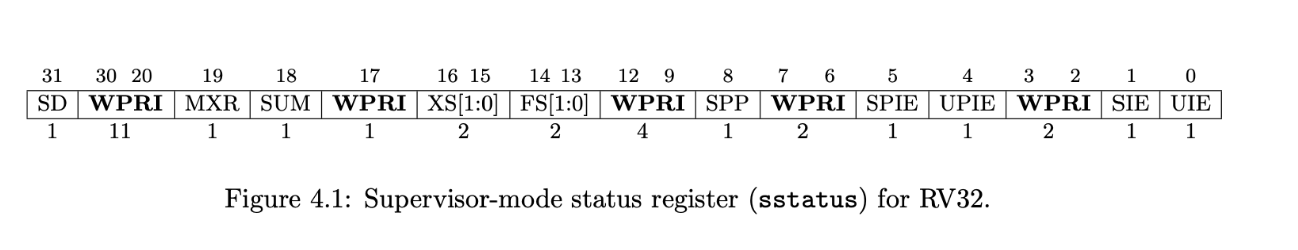
- sstatus:
- SIE: Control whether device interrupts are enabled. If the kernel clears SIE, the RISC-V will defer device interrupts until the kernel sets SIE.
- SPP: Indicate whether a trap came from user mode or supervisor mode, and controls to what mode sret returns.
- satp: holds the address of the pgtbl root
- The RISC-V hardware does the following for all trap types when it needs to force a trap
- If the trap is a device interrupt, and the sstatus SIE bit is clear, don’t do any of the following.
- Disable interrupts by clearing the SIE bit in sstatus.
- Copy the pc to sepc
- Save the current mode (user or supervisor) in the SPP bit in sstatus.
- Set scause to reflect the trap’s cause
- Set the mode to supervisor.
- Copy stvec to the pc.
- Start executing at the new pc.
Note that CPU doesn’t switch to the kernel pgtbl, neither a stack in kernel, and doesn’t save any registers except the PC, which should be done by kernel software.
Traps from user space
A trap may occur while executing in user space if the user program makes a system call (ecall instruction), or does something illegal, or if a device interrupts.
- when a trap occurs, which code blocks shoud be executed
- uservec(kernel/trampoline.S:16): The high-level path of a trap from user space
- usertrap(kernel/trap.c:37):
- usertrapret(kernel/trap.c:90): when returning
- userret(kernel/trampoline.S:88):
- Trampoline:
- It is mapped in the user page table, with the PTE_U flag, traps can start executing there in su- pervisor mode.
- It is mapped at the same address in the kernel address space, the trap handler can continue to execute after it switches to the kernel page table.
If the trap is a system call, usertrap calls
syscall to handle it; if a device interrupt, devintr; otherwise it’s an exception, and the kernel kills the faulting process.Traps from kernel space
- what should kernel do before handling the trap?
- set stvec points to kernelvec
- satp points to the kernel pgtbl
- stack point points to a vaild kernel stack
- when a trap occurs, what code blocks should be executed?
- kernelvec copys the 32 registers on the stack, and jump to
kerneltrap() kerneltrap()executes trap handling, and returns to kernelveckernelvec()set the 32 registers from stack
kernelvec copys the 32 registers on the stack of interrupted kernel thread
code
- usertrap()
- Determine the cause of the trap, process it, and return
- Changes stvec so that a trap while in the kernel will be handled by kernelvec rather than uservec
- It saves the
sepcregister (the saved user PC), becauseusertrapmight callyieldto switch to another process’s kernel thread, and that process might return to user space, in the process of which it will modifysepc. - 首先检查trap是否来自user mode
- 改变stvec值指向kernelvec而不是userevec,从而将后续trap类型为interrupts和exception交给
kerneltrap() - 保存spec中的user pc,usertrap可能会调用
yield(),改变到另一个process‘s kernel - 判断trap的类型,syscall则交给
syscall()处理,否则就是异常,kernel杀死该进程 - syscall()执行前将trapframe→epc += 4
usertrap()结束之前,检查该进程是否被杀死,如果是timer interruption需要让出cpu
- kerneltrap()
- 首先检查sstatus的SPP位,确认trap来自supervisor mode,检查SIE
- 调用
devintr(),检查是timer interrupt,device interrupt或者exception - device interrupt:调用
uartintr()或virtio_disk_inte()进行进一步的处理 - time interrupt:return 2,调用
yield() - 无法识别:返回0并panic
- 当等到CPU有机会运行我们的thread,则会继续运行
kerneltrap() kerneltrap()结束后,需要返回之前,需要恢复spec和sstatus,这两个寄存器可能以为yield()导致里边存放的是脏值。然后返回到kernelvec汇编代码- 最后返回到
kernnelvec,恢复并返回the interrupted kernel code
- usertrapret()
- 准备工作,关闭中断
- 设置stvec指向uservec
- 为process将来的trap设置好trapframe,恢复pgtbl,stack,hartid等
- spp设置为0,恢复中断
- p→trapframe = user pc
- 调用uerret
用于返回用户空间
- uservec
- The
csrrwinstruction at the start of uservec swaps the contents ofa0andsscratch. Now the user code’s a0 is saved in sscratch; uservec has one register (a0) to play with(a0 is avaliable now); and a0 contains the value the kernel previously placed in sscratch. - Save the 32 user registers. Before entering user space, the kernel set sscratch to point to a per-process trapframe structure that (among other things) has space to save the 32 user registers
- save 32 general registers
- load the kernel’s pgtbl, stack, current cpu id into relavent registers
- jump to usertrap() and execute the c code
- sret
- enable int
- copy sepc to pc
- set mode to usermode
- start executing at the new pc
与ecall刚好相反
- userret
- 传入的参数中,a1存放指向process‘s用户态页表的指针,首先交换a1和satp,调用汇编指令切换到user pgtbl
- a0存放TRAPFRAME,将a0值存在t0,然后存到sscratch中
- 恢复现场,从trapframe中恢复除了a0之外所有寄存器的值
- 交换sscratch和a0的值,恢复a0,将trapframe保存到sscratch,为下一次的trap做好准备
- 执行sret指令
主要完成从kernel到user的完整切换
- ecall
- 如果trap是设备中断,且SIE位被清空,则不执行任何指令
- 清除SIE位以禁止中断
- U mode → S mode
- spec = pc
- pc = stvec
- jump to pc
- 将当前的mode保存在SPP中
- 作者:GJJ
- 链接:https://blog.gaojj.cn/article/blog-84
- 声明:本文采用 CC BY-NC-SA 4.0 许可协议,转载请注明出处。








